These files and their associated. Please see the references for more information. For more information about how to contact Microsoft for support issues, visit the International Support Web site. Other versions or editions are either past their support life cycle or are not affected. In no event shall Microsoft Corporation or its suppliers be liable for any damages whatsoever including direct, indirect, incidental, consequential, loss of business profits or special damages, even if Microsoft Corporation or its suppliers have been advised of the possibility of such damages.
| Uploader: | Sabar |
| Date Added: | 5 August 2012 |
| File Size: | 62.61 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 35025 |
| Price: | Free* [*Free Regsitration Required] |
Customers who require custom support for older releases must contact their Microsoft account team representative, their Technical Account Manager, or the appropriate Microsoft partner representative for custom support options. Best practices recommend that systems that are connected to the Internet have a minimal number of ports exposed.
If you have any questions or need further information, please contact them directly.
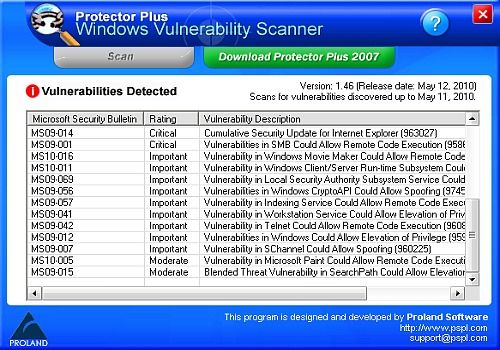
MS Vulnerabilities in SMB Could Allow Remote Code Execution ()
If downloading at a later date, it is recommended that the bulletin is retrieved directly from the author's website to ensure that the information is still current. Where are the file information details? An attacker who successfully exploited these vulnerabilities could install programs; view, change, or delete data; or create new accounts with full user rights.
In no event shall Microsoft Corporation or its suppliers be liable for any damages whatsoever including direct, indirect, incidental, consequential, loss of business profits or special damages, even if Microsoft Corporation or its suppliers have been advised of the possibility of such damages. The mailing list you are subscribed to is maintained within your organisation, so if you do not wish to continue receiving these bulletins you should contact your local IT manager.
Several Windows services use the affected ports. What is the scope of the vulnerability? The vulnerability is caused by the Microsoft Server Message Block SMB Protocol software insufficiently validating the buffer size before writing to it.
All product names, logos, and brands are property of their respective owners. QFE service branches contain hotfixes in addition to widely released fixes.
Microsoft Security Bulletin MS09-001 - Critical
Use of these names, logos, and brands does not imply endorsement. An attacker who successfully exploited these vulnerabilities could install programs; view, change, or delete data; or create new accounts with full user rights. An attacker who imcrosoft exploited this vulnerability could cause the attacker to take complete control of the system.
Other versions or editions are either past their support life cycle or are not affected. To improve security protections for customers, Microsoft provides vulnerability information to major security software providers in advance of each monthly security update release.
The vulnerabilities could allow remote code execution on affected systems. Most attempts to exploit this vulnerability will cause an affected system to stop responding and restart. When this security bulletin was issued, had Microsoft received any reports that this vulnerability was being exploited?
Further manipulation can theoretically result in remote unauthenticated code execution. An attacker who successfully exploited this vulnerability could cause the computer to stop responding and restart.
Microsoft Security Bulletin MS - Critical - Ars Technica OpenForum
SYS driver of the Windows operating system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. If you continue to browse this site without changing your cookie settings, you agree to this use.
What should I do?
When this security bulletin was issued, had this vulnerability been publicly disclosed? To determine the support life cycle for your software version or edition, visit Microsoft Support Lifecycle. Microsoft recommends that you block all unsolicited inbound communication from the Internet to help prevent attacks that may use other ports. Microsoft has tested the following workarounds and states bullein the discussion whether a workaround reduces functionality: These ports are used to initiate a connection with the affected component.
Products The Rapid7 Insight Cloud.
For more information on this installation option, see Server Core. How could an attacker exploit the vulnerability?
The attributes of these security files are not listed. The affected software listed in this bulletin have been tested to determine which releases are affected.

No comments:
Post a Comment